ThinScale Technology has always been at the forefront of endpoint security, specifically in breach & data leakage prevention. Securing endpoints ensures that even pre-existing malware is prevented from running on ThinScale machines. But what about end users who decide to try to circumvent this security? How can IT teams ensure a user with valid credentials does not access their corporate resources from an unsecured machine?
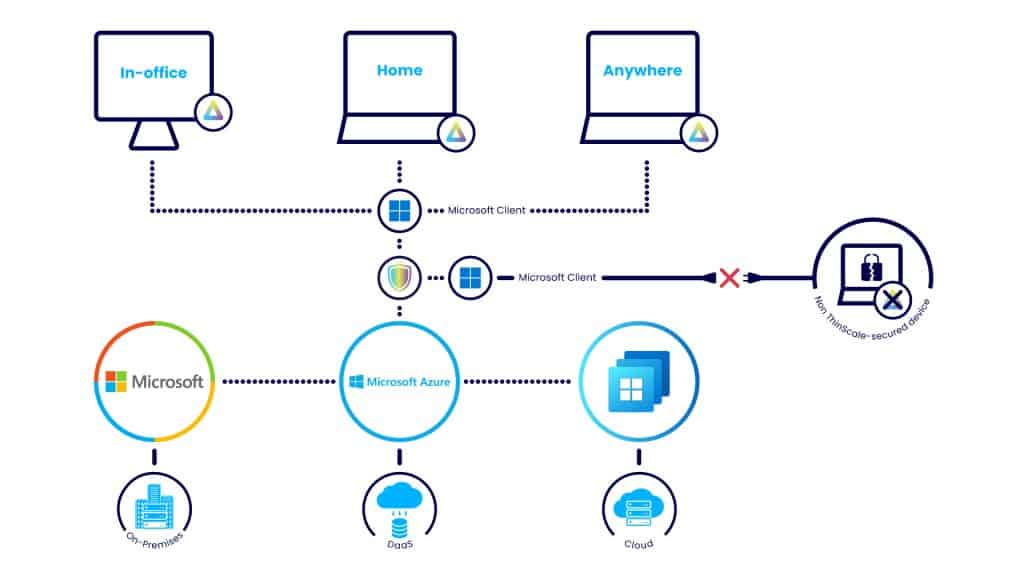
ThinScale’s Virtual Desktop Agent (VDA) actively prevents any unsecured machine, not actively running a ThinScale workspace, from connecting to the VDI or DaaS environment in question.
Functionally the VDA acts as a final check on the security and validity of the device attempting to access corporate virtual environments.
How does it work?
The Virtual Desktop Agent facilitates communication between the endpoint and VDI, allowing IT to specify rules to occur at the virtual desktop level depending on the information it reads from the endpoint.
The Virtual Desktop Agent can tell when a user is trying to connect to a virtual machine from a non/inactive ThinKiosk/Secure Remote Worker device and can allow or deny connections based on this with preconfigured rules. Without this, users could easily bypass even the most locked-down endpoint environments by using their corporate credentials on a browser on another device. Through the Virtual Desktop Agent, this is now impossible.
An example of this in action would be where a company has a number of both on-prem and home workers; the Virtual Desktop Agent can make it so the home workers on personal devices cannot access their virtual environment unless connecting from Secure Remote Worker, allowing complete security for your end users when working out of the office.
Admins can even set up the VDA to allow only connection from specific ThinKiosk or Secure Remote Worker profile names, further ensuring strict access control even when credentials may be compromised.
Where does the VDA work?
The VDA is installed on the host of the virtual machine, though the control of it can be accessed via the ThinScale Device Portal if using ThinScale Cloud, or the ThinScale Management Platform if using a hosted management environment.
Conclusion
The VDA provides IT control over corporate resource access regardless of deployment or type of work by restricting end-users to accessing these resources only through ThinScale-secured devices. It even reinforces MFA policy by acting as another automated barrier to entry even if credentials are compromised.



