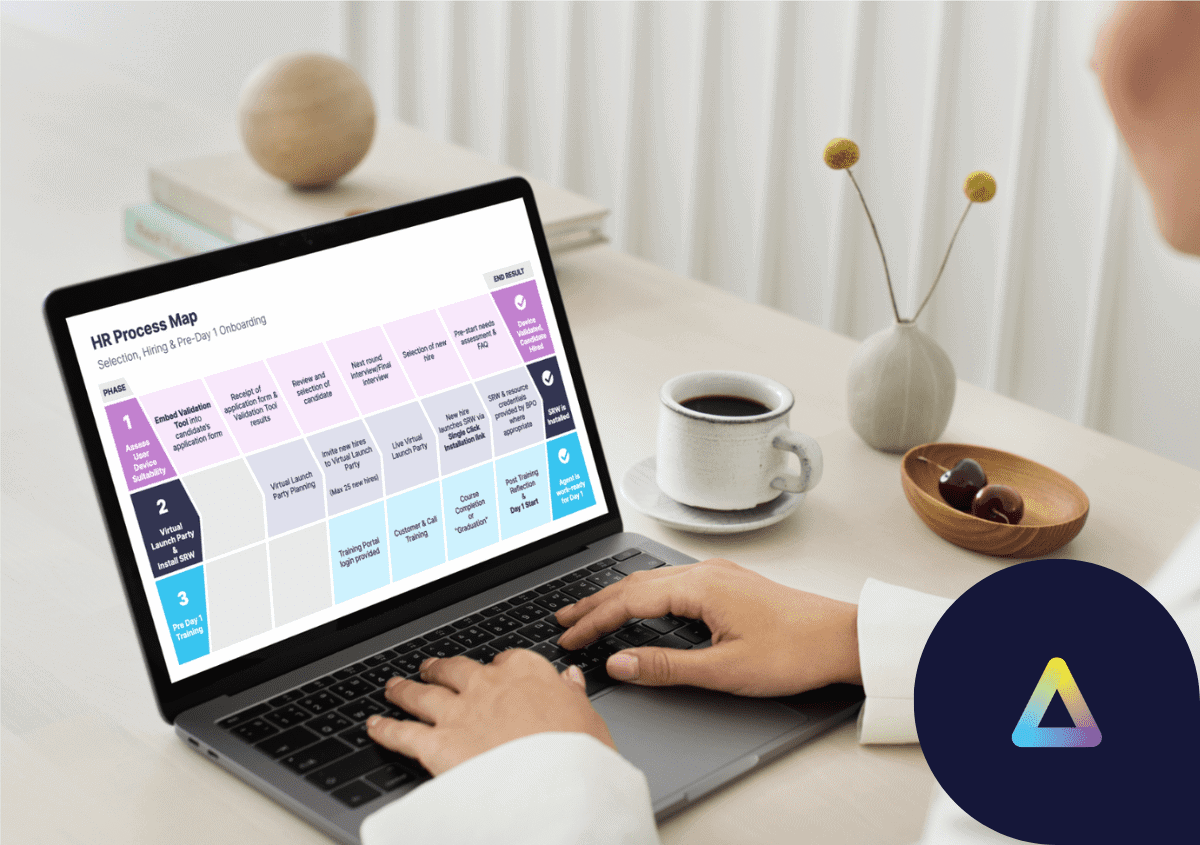
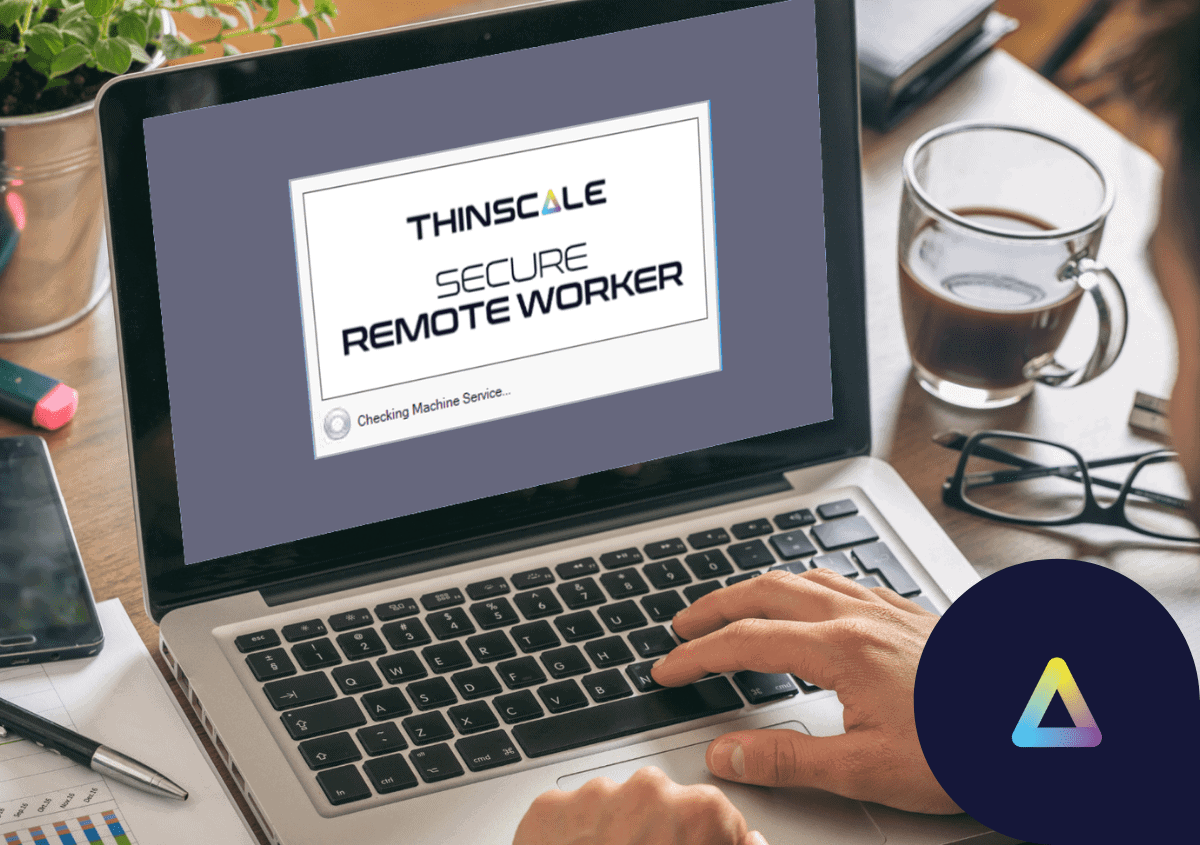
USBs (as well as most hardware) by their nature always have a possibility for failure, or damage and are dependent on logistics that we have seen are easily disrupted organizations are modernizing their infrastructure because the workforce is no longer within 10 Kilometres of the main office, where employees can span past international borders. We would go as far as to say mounting an OS on a USB and sending it to your remote employees is akin to stubbornly only using CDs when music streaming platforms are more convenient and efficient. So why are companies abandoning USB-mounted operating systems?
 Peter Corish
Peter Corish
Go Green: Recycle, Repurpose and Reuse Hardware with ThinKiosk
How repurposing existing IT hardware not only increases your ROI but decreases your organization’s carbon footprint. Why repurpose old IT hardware? Electronic Waste (E-Waste) is the worlds largest waste stream according to the 2020 UN Global E-waste Monitor, with over 53.6 million metric tons of e-waste accumulated in 2019 alone, with only 17.4% of that … Read more
Zero Trust: modernize your endpoint security
Modern IT infrastructure is exposed to a large amount of risk, with the frequency of cyber-attack rising year on year. Hybrid working, which is becoming a mainstay for most organizations, increases the attack surface for organizations due to corporate accessing endpoints (e.g. laptops) moving outside of the organization’s direct control.
How to Effectively Manage a Remote or Hybrid Contact Center Workforce
During the pandemic, the BPO industry confronted a serious dilemma — maintaining business continuity in the face of a global pandemic that required closing physical contact centers. The solution came in the form of a virtual remote workforce with agents working from home, often using their own devices.
How Much is Agent Attrition Really Costing you?
The Great Resignation. You often hear that term used to explain the high rate at which employees quit their jobs in 2021. However, that term is not new to the contact center industry. It has experienced a “great resignation” in the form of agent attrition for years. Historically, contact centers have seen attrition and turnover … Read more
Optimising WaH/Hybrid with Secure BYOD
A full-time return to office-based work looks highly unlikely, at least for the foreseeable future.
Hybrid Work: Simple, Secure and Cost-Effective
Hybrid environments have been correctly identified as the way forward for the majority of organizations. However, some have identified complications around ease of implementation, with multiple solutions to manage and their associated costs (server allocation, hardware and software acquisition, etc.) The question is, how can you deliver hybrid/work from anywhere quickly, seamlessly, and with as … Read more
How Secure Are Your Outsourcers? Ensuring End to End Compliance
Outsourced customer experience (CX), business process outsourcing (BPO), and contact centre providers have long championed their ability to adhere to data protection and privacy regulations strictly. However, with seasonal contact centre scaling, a COVID-related surge in outsourced projects, and a seismic influx of customer data comes an increase in security and compliance risks on both … Read more
Got employees WFH? These are the risks to protect them and you from.
The fear of a security breach occurring on their watch is sure to keep IT admins up at night. Nowhere are the chances of that happening more pronounced than in a Work at Home (WaH) environment. Remote working is not going away, however. COVID-19 made it an operational imperative, and it provides many benefits to … Read more
Does your Contact Center have the right Endpoint Security solution?
At ThinScale technology, we work closely with customers in the contact center industry and have seen some confusion around the various endpoint security solutions available. What can they each do? And more importantly, from a security perspective, what do they not do? This article I’ll take you through each of the major endpoint security solutions … Read more