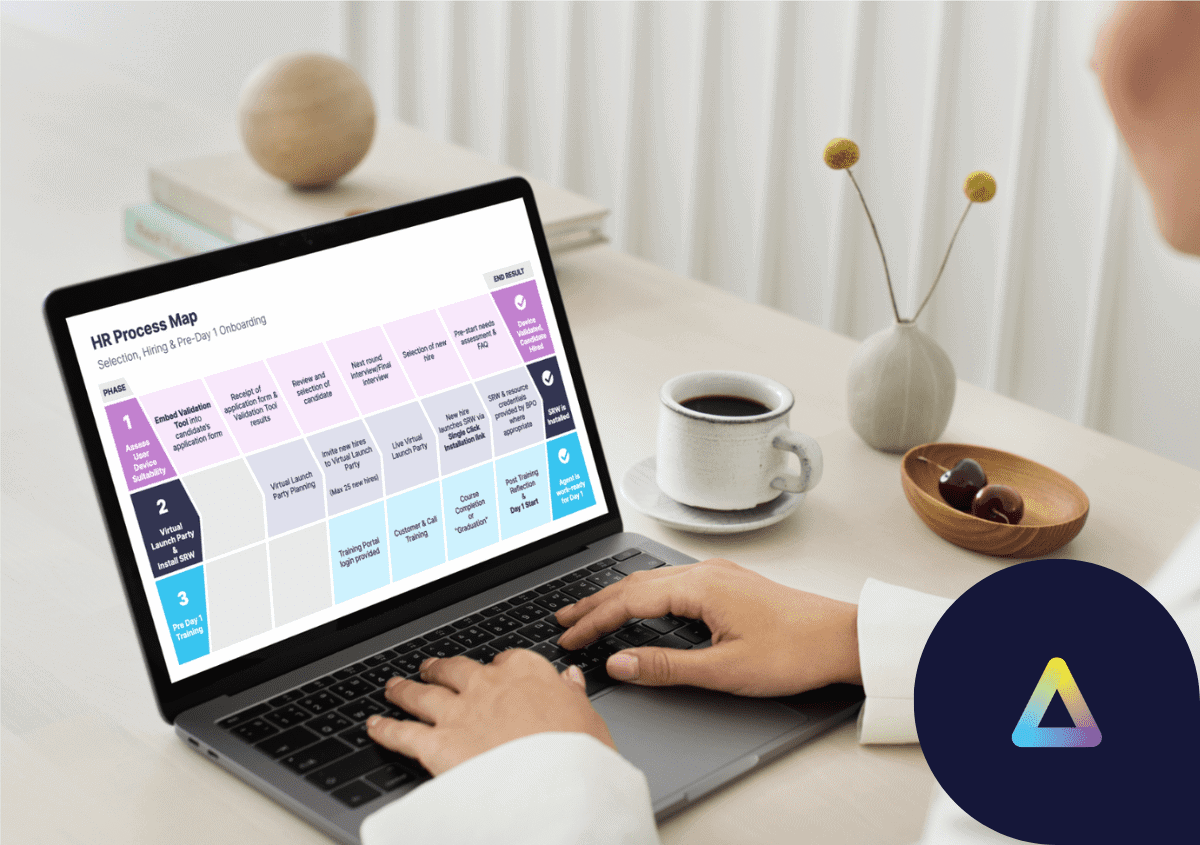
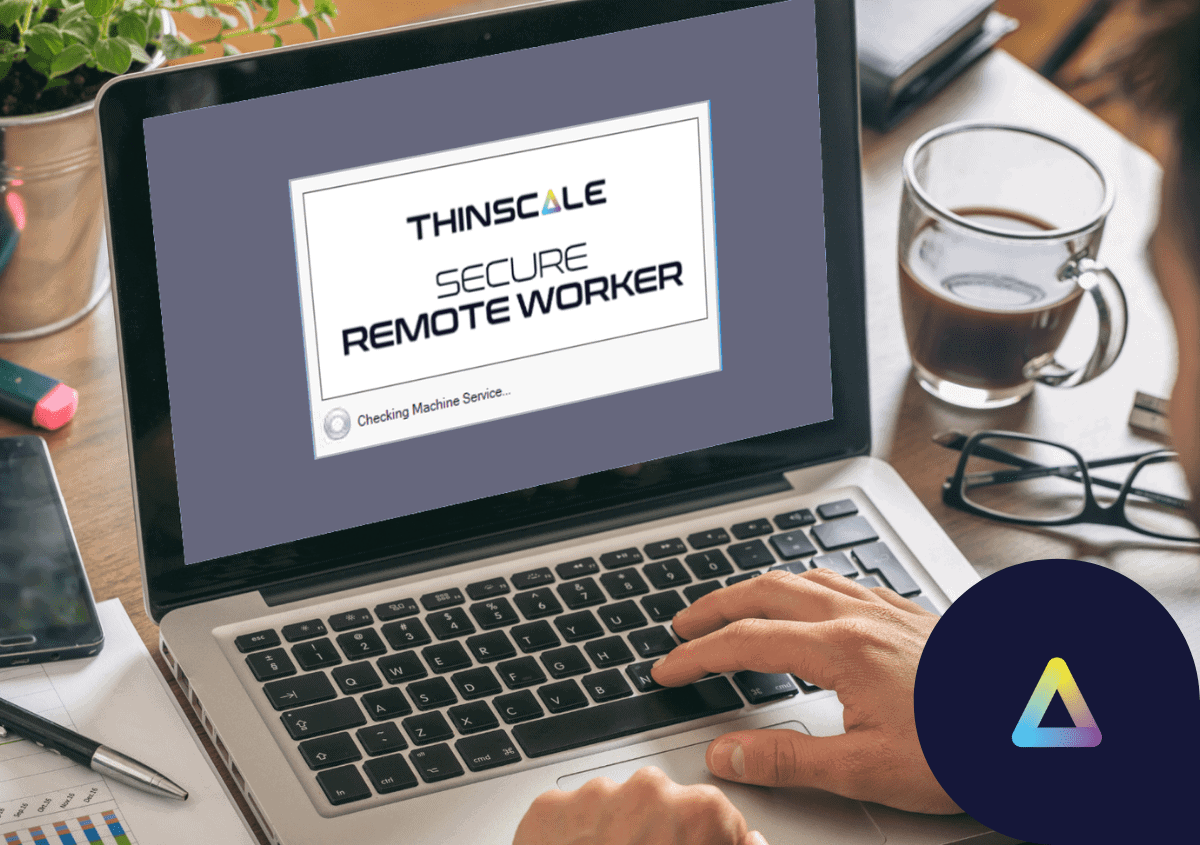
Seasonal surges are par for the course in the BPO and contact center industries. In just a few weeks, the new agent headcount can go from a few hundred to a thousand. For the bigger BPOs, the numbers are even more staggering.
Remote Working
Go Green: Recycle, Repurpose and Reuse Hardware with ThinKiosk
How repurposing existing IT hardware not only increases your ROI but decreases your organization’s carbon footprint. Why repurpose old IT hardware? Electronic Waste (E-Waste) is the worlds largest waste stream according to the 2020 UN Global E-waste Monitor, with over 53.6 million metric tons of e-waste accumulated in 2019 alone, with only 17.4% of that … Read more
Zero Trust: modernize your endpoint security
Modern IT infrastructure is exposed to a large amount of risk, with the frequency of cyber-attack rising year on year. Hybrid working, which is becoming a mainstay for most organizations, increases the attack surface for organizations due to corporate accessing endpoints (e.g. laptops) moving outside of the organization’s direct control.
The Benefits of Work at Home/BYOD for Hiring Managers
It should come as no surprise to contact center human resources directors that one of the best recruiting benefits the work at home (WaH) agent model offers is hiring without geographic limitations. Couple that with allowing agents to use their own devices (BYOD), and you make the job even more attractive to prospective candidates.
How to Effectively Manage a Remote or Hybrid Contact Center Workforce
During the pandemic, the BPO industry confronted a serious dilemma — maintaining business continuity in the face of a global pandemic that required closing physical contact centers. The solution came in the form of a virtual remote workforce with agents working from home, often using their own devices.
Attn: Contact Center Executives – There is Gold Beneath Your Feet
Andrew McNeile, Chief Customer Officer (ThinScale)
How Much is Agent Attrition Really Costing you?
The Great Resignation. You often hear that term used to explain the high rate at which employees quit their jobs in 2021. However, that term is not new to the contact center industry. It has experienced a “great resignation” in the form of agent attrition for years. Historically, contact centers have seen attrition and turnover … Read more
Optimising WaH/Hybrid with Secure BYOD
A full-time return to office-based work looks highly unlikely, at least for the foreseeable future.
Hybrid Work: Simple, Secure and Cost-Effective
Hybrid environments have been correctly identified as the way forward for the majority of organizations. However, some have identified complications around ease of implementation, with multiple solutions to manage and their associated costs (server allocation, hardware and software acquisition, etc.) The question is, how can you deliver hybrid/work from anywhere quickly, seamlessly, and with as … Read more
How Secure Are Your Outsourcers? Ensuring End to End Compliance
Outsourced customer experience (CX), business process outsourcing (BPO), and contact centre providers have long championed their ability to adhere to data protection and privacy regulations strictly. However, with seasonal contact centre scaling, a COVID-related surge in outsourced projects, and a seismic influx of customer data comes an increase in security and compliance risks on both … Read more